Setting up HSTS in Cloudflare
- Nabu

- Apr 19
- 1 min read
Updated: Apr 21
One of the more common vulnerabilities found during ASV scan is the lack of HSTS (HTTP Strict Transport Security). This is not necessarily limited to your application server; HSTS should be setup in all internet-facing hosts that provide path to, or are part of the cardholder data environment (CDE).
This includes the WEB Application Firewall (WAF), and one of the most common ones is Cloudflare (Cloudflare™ is a registered trademark of Cloudflare, Inc.) A common problem found in ASV is that HSTS was not set for the Cloudflare WAF.
Luckily, it is easy to fix it. Follow these steps:
Log into Cloudflare at https://dash.cloudflare.com.
Click on the domain where you want to enable HSTS.
In the sidebar or top menu, click “SSL/TLS” / “Edge Certificates”:

Enabling HSTS in Cloudflare Scroll Down to ‘HTTP Strict Transport Security (HSTS)’
Click “Enable HSTS” (you might see a warning first—acknowledge it if needed).
You’ll see several options:
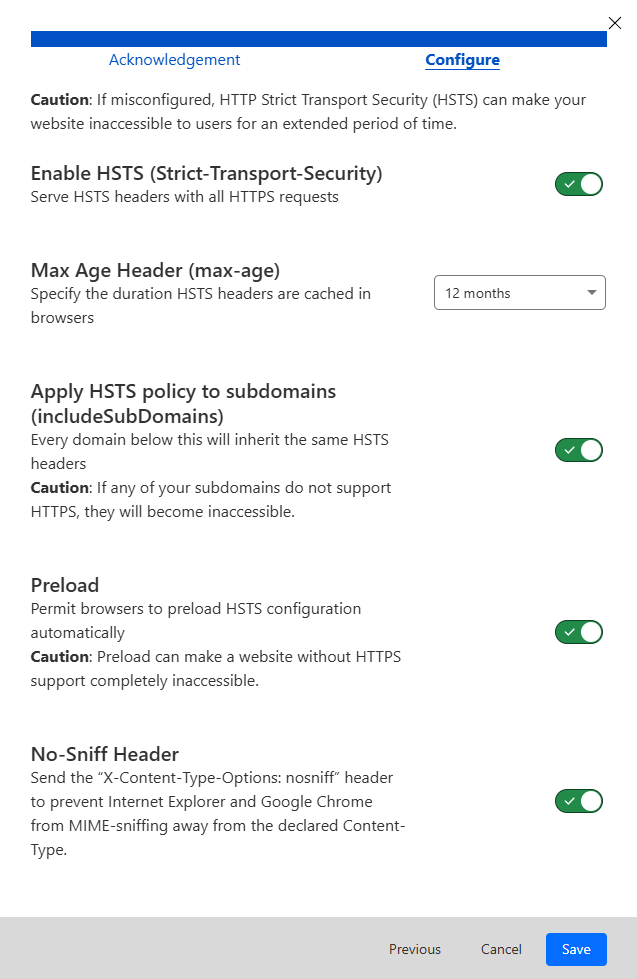
Max Age Header (seconds): This is how long browsers should remember to use HTTPS; Recommended setting: 1 year / 12 months.
Include subdomains: Applies HSTS to all subdomains too. Recommended setting: Yes.
Preload (optional): Adds your site to browser preload lists. If you check it, you’ll need to submit your domain manually to the preload list here: https://hstspreload.org.
Note that once preloaded, it’s difficult to remove your domain from the list.
No-Sniff Header: Adds extra security by preventing MIME-type sniffing.
Apply HSTS to HTTP: Forces HTTP requests to redirect to HTTPS. Recommended setting: Yes.
Click “Save”

